Splunk Event Logging Transport
The Splunk Event Logging Transport pushes Transaction Data into Splunk as a standard log event via HTTP. It executes similar to the Splunk Event Logging Processor, but logs events from Transaction Data instead of configuration string.
Configuration
Configuration is done via the Basic, Advanced, and Connection tabs, and is similar to the Splunk Event Logging Processor’s configuration.
Basic Tab – The Basic tab contains the following configuration options:
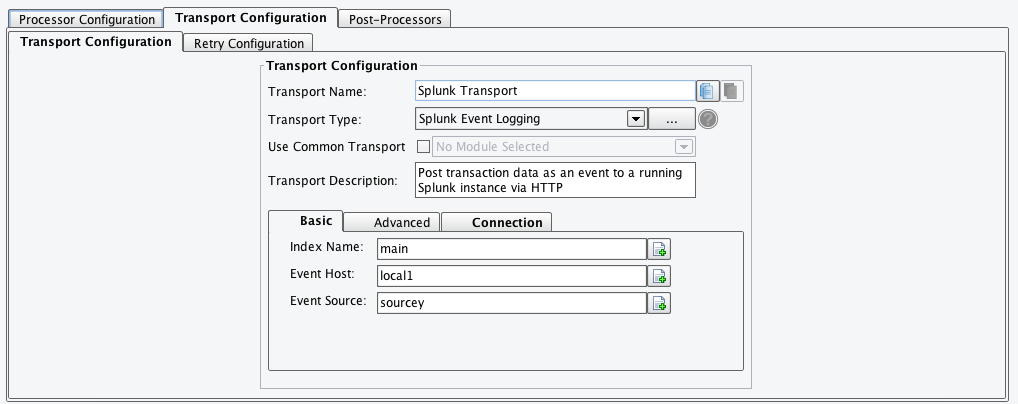
- Index Name: The name of the Splunk Index to apply this message to. It will be dependent on your particular Splunk instance, but ‘main’ is the standard index for a default installation.
- Event Host: The name of the event host this message is coming from. Can be left blank or provided a custom value.
- Event Source: The name of the event source for this message. Similar to the event host, can be left blank if desired.
Advanced Tab – The Advanced tab contains the following configuration options:
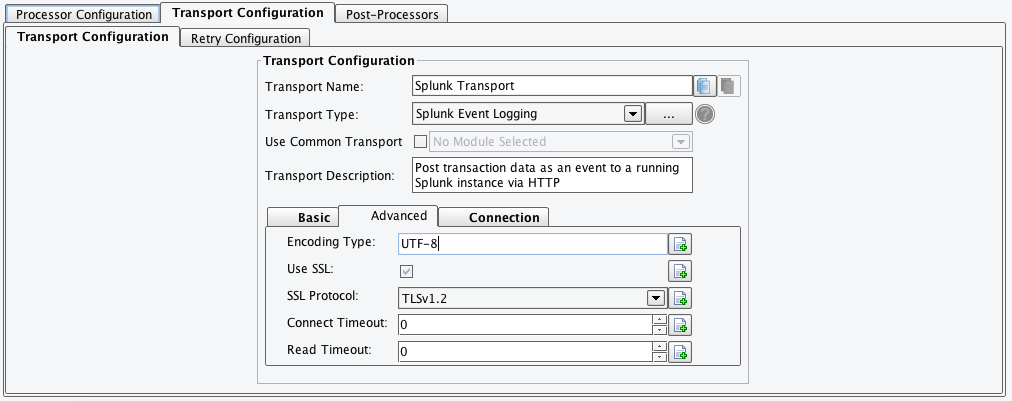
- Encoding Type: The encoding to use when collecting the Transaction Data for transfer to Splunk. When in doubt, use the default ‘UTF-8’.
- Use SSL: Select if the connection to Splunk should use SSL. The default is true.
- SSL Protocol: Select the SSL protocol to use when connecting securely to Splunk. The default is ‘TLSv1.2’.
- Connect Timeout: The time in seconds to wait before failing to make a Splunk connection. The default value of 0 means no timeout.
- Read Timeout: The time in seconds to wait before timing out the Splunk connection. The default value of 0 means no timeout.
Connection Tab – The Connection tab contains the following configuration options:
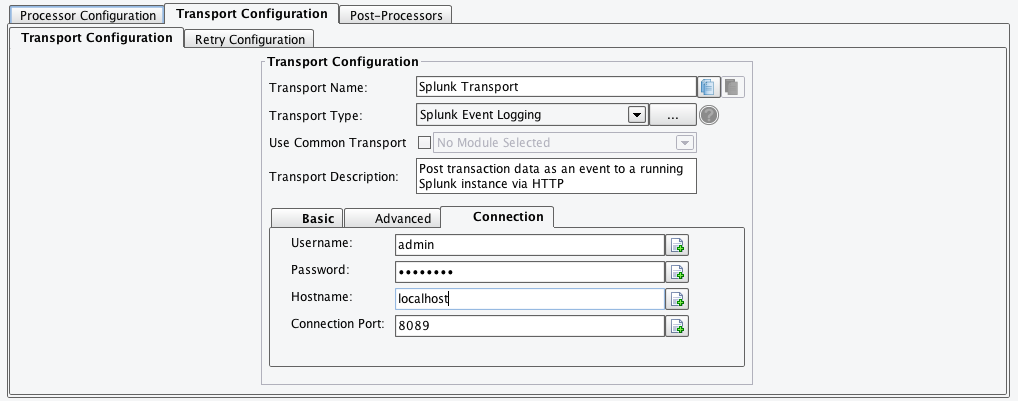
- Username: The username of the Splunk user to connect as.
- Password: The Splunk user’s password.
- Hostname: The hostname of the Splunk instance to connect to.
- Connection Port: The Splunk instance connection port. The default value is 8089.
